There has been so much coverage of high-profile ransomware incidents in the news lately, but the coverage I see in most circles continues to discuss them as individual events. And some days, I just can’t help thinking like an old Intelligence Analyst.
Maybe I’m just gettin’ old and becoming a conspiracy theorist – or maybe that time spent analyzing Russian activity back in the cold war is still useful for something. Time will tell, I suppose, but here’s what I see when I look at all this.

Ransomware As We Know It
Like most malware, this started out as a tiny little corner of the market, mostly randomly distributed – bad website link here, infected file there. Infect a machine, and hope the person would pay. Then someone saw the potential and started systematizing it. Short version: today, ransomware is a software market like any other. Organizations host it, provide services and support for it, and lease it to third parties. The third-party does the work of getting it out there, and the host takes a cut of the ransom.
In its most recent iteration:
- Instead of immediately encrypting the machine it lands on, ransomware is tuned to silently drop network tools on that machine, and use it to ‘discover’ the rest of its network, giving attackers time to assess the value of the target, and the ransom to demand.
- Attacks are often targeted, for example spam-blasting a large organization knowing that if you can reach hundreds of users, eventually one of them will click the link.
- The model has shifted toward double extortion: In addition to charging for the decryptor, organizations now often charge separately to not-release your stolen data.
This is more than just ‘ransomware getting uglier’. It’s what happens when a hobby becomes a business. A multi-billion-dollar industry, in fact. It’s even beginning to show some of the cracks that appear in businesses that grow quickly. Ransom collections depend on being known as “honorable thieves” who provide the goods when paid. But some short-sighted subcontractors have begun to “double-dip” – charging to not release data, then coming back months later to demand payment again. In time, this causes customers to simply take the hit, knowing that paying won’t really guarantee safety. The astronomical rise in ransom amounts has finally begun to concern insurers as well, and offending powerful monied interests will have repercussions. Just as with other businesses, short-sighted profiteering may cause it to collapse.
Ransomware As A Trial Balloon
When the SVR (Russian Intelligence) infiltrated SolarWinds, they started small – a tiny bit of code that read processor information and sent it home. Meaningless, in and of itself. A proof of concept: we can insert code without being seen, and piggyback the application’s usual communication channels to send data home without being noticed. The next round was 3500 lines of elegant, spare code that sent home information about the networks it infiltrated, allowing the SVR to concentrate their human labor, lurking and monitoring the highest value targets, including a dozen federal agencies. Analysts say the code wasn’t written “to” SolarWinds – it was crafted in a fashion that would allow it to be leveraged against multiple platforms. If it worked, it could go anywhere. The processor reader utility was a trial balloon to test the viability of the larger concept. One can’t help but wonder what the final product might serve as a trial balloon for.
Pandemic and Ransomware
During the global pandemic, as millions of workers shifted overnight to telecommuting, and government and health services became essential lifelines, ransomware rose logarithmically. Each week brought news of new attacks, ever-increasing ransoms, and new data breaches. Accustomed to the random nature of malware, the American public read each of these as an individual event – an unfortunate accident that happened to strike where it did. But we know that, for example, Darkside conducts targeted attacks. That an Eastern European operation intentionally targeted hospitals in December 2020. And that the Russian intelligence services intentionally targeted SolarWinds, a network management software company that listed many of its clients on its website (that list has since been removed).
And yet – we continue to think of these as isolated incidents.
When President Biden admonished Vladimir Putin to address ransomware activities centered in Russia, most Americans seem to assume the reason was “that’s costing a lot of time and money. It’s about time they put a stop to it.” Insurance companies are tired of the escalating ransom costs. Businesses can’t afford the lost revenue.
Money may be a reason but it certainly isn’t the reason. These events constitute a potentially existential attack on our population.
Zooming Out
Let’s look at this from a slightly broader perspective. Just as the world became embroiled in a pandemic, Russia infiltrated SolarWinds. In February, they stealthed their way into countless networks. As our government scrambled to respond to changing conditions, the SVR lurked quietly – quite possibly reading every significant email and internal, eyes-only report flowing through several critical federal agencies.
Meanwhile, rEvil and Darkside, a splinter group that may be a former rEvil faction, wreaked havoc. These businesses move in a complex dance with the Russian government, and on any given day it’s possible that their activities are independent of, in complement to, or even commissioned by the SVR. Events could be simpler than that – like earlier American Robber Barons who made millions in war profiteering, these organizations may just be “pandemic profiteering.” But those activities provide a great smokescreen, diverting cyber resources to active, visible threats and causing us to miss the connections between three early reports that might otherwise have led them to SolarWinds.
How an Individual Attack Can Land at the Center of Statecraft
Those independent entities – whether or not they are acting under the guidance of their government – are still at the center of current diplomacy. Let’s look at two recent attacks from that perspective.
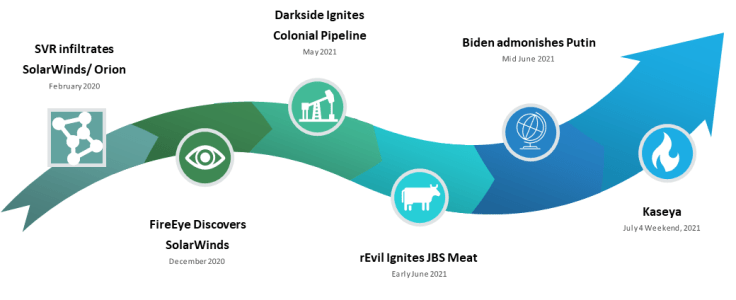
Darkside’s Colonial Pipeline attack was a brilliant victory for Russia. They disabled a major pipeline, stopped fuel from flowing through a huge portion of the US, created a brief energy panic, and got away with a huge ransom. But the worst part – or the best, if you’re a Russian – was knowing that we couldn’t do anything about it. Sure, the Russians have pipelines. But they know we can’t attack them.
Colonial was an American-owned pipeline, in the USA, serving millions of Americans. The Russian pipeline is a totally different story. It carries gas to Russians, sure – but also to our allies. The EU imports about 60% of its energy resources – and more than half of its coal, oil, and natural gas comes from Russia. Shutting down the Russian pipeline is an attack on Russia’s economy – but it’s an attack on the operational structure of dozens of US allies, too.
Bet that victory tasted sweet. сладкий как сахар*
But hey – at least we managed a little score, getting some of the money back, right? Actually, that’s a pretty big deal too.
Most currencies are ‘reliable’ because they are backed by a stable government that promises to redeem its tender. Cryptocurrencies are developed on the basis that one doesn’t need a government for that – the security and reliability of the blockchain are its guarantees. So when the FBI broke into it and took some of the money back – they effectively called the entire basis of cryptocurrency into question. And cryptocurrency is the basis of the ransomware economy.
Move. Countermove.
But that countermove was a little subtle – so a few weeks later Joe Biden shook his finger at Vladimir Putin and said “y’know, you’re just letting these criminals operate in your borders and if you don’t do something about it I’m gonna have to.” Sound like Old White Guy Posturing? You might want to bear in mind that this was exactly the conversation we had with Afghanistan over protecting bin Laden from criminal prosecution – and that one led to the longest war in American history.
Now, Putin could have responded by having the SVR pull a thread somewhere. They surely have more “stuff” inside those compromised agencies. They knew SolarWinds would get exposed eventually, and I’m hard-pressed to believe they just complacently waited for that to occur, without making an effort to leave any other hooks in those networks. But – assets like that are most useful when they remain concealed and it’s unlikely that Putin wanted to escalate officially. A US President – especially one who might be feeling the need to counterbalance his predecessor’s Russian relationships – could respond…strongly. Russia’s not in great pandemic shape and Putin doesn’t need to risk losing a PR War. No, this calls for an unofficial response – one that can be disavowed.
As luck would have it, such a response arose almost immediately!
On July 4 weekend – the celebration of American strength and independence – rEvil mounted the largest, most widespread ransomware attack in history. While the nature of the attack meant it affected multiple nations, the vast majority of the affected businesses just happened to be American. Reports give a range from 800-1500 businesses, but Sophos estimated it closer to 2,000. That would have been enough of an impact to make the point: rEvil doesn’t think Joe Biden should be scolding Putin for their work.

Just protecting their market segment? Or a direct diplomatic response to the implied threat in Biden’s words? Just in case you were in doubt, rEvil went out of their way to make it clear.
Rather than leveraging their historic practices, rEvil launched a supply-chain attack on a network services provider – directly mimicking SVRs attack on SolarWinds. But the activity was all done by a non-government entity, so in terms of statecraft, it was just a random crime, and although that crime looks almost exactly like the last SVR digital attack we saw – it wasn’t them. Nothing can be laid directly at the feet of the Russian government.
сладкий как сахар
But over the past year, the FBI has had lots of opportunities to watch, track, and trace rEvil. The countermove was beautiful. Based on the timing, I’d guess Kaseya had time to either figure out its recovery plan – or pay its ransom and get its decryptor and validate that it worked. And then – rEvil disappeared.
I wondered, as I first read reporting on this, whether they had ‘retired’. Ransomware teams often do. After taking in enough cash, they shut down and some members retire while others go on to start new operations – just as Grand Crab shut down and gave birth to rEvil. But then I read the description and it was clear that rEvil didn’t close its operation. Every server went offline at the same time, and their DNS was scrubbed from parts of the net. That was done to them.
Wonder if the FBI will get any of Kaseya’s money back…
Move. Countermove.
Zooming Out A Little More
Ransomware, sure. How about social media? Or do we figure it’s pure coincidence that the USA, France, Britain, and Germany all had simultaneously successful extremist-right shifts at the same time? And that much of that shift was fueled by social media which, in many cases, has been tied back to Russian troll farms? (Not, of course, operated by the government. Well, except that one place…)
There’s certainly an argument to be made that Putin, who has long been a visionary regarding the potential of the internet for cyberwarfare (he was discussing the possibilities back in the mid 90s) is simply working a plan. He consolidated his own position in Russia, then started working on his world position. That, having reached the pinnacle of his ability and still not finding himself at an even height with the rest of the west – he started working to bring them down to his level. If you can’t get to the top by climbing, get there by shaving the mountaintop down a little, right?
In that plan, combining a social media assault on the populace (which helpfully achieves destabilization in government) with ransomware to destabilize business would be a brilliant one-two punch.
But of course, that’s crazy. We’ve gone from a really interesting exploration of the implications of ransomware to a tinfoil hat conspiracy theory now, haven’t we? Yes, there’s a real threat from ransomware but the other stuff, the older stuff, was just folks playing with the system and learning how things work to prepare for an effort like this maybe. I mean, it’s not like this has been going on for years.
Oh, wait. China, hacking the federal personnel files to take security clearance investigation data. That was 2015 – and they also took fingerprint data, and records of every journalist who had entered federal buildings.
The Director of the NSA says there has been a 17-fold increase in cyber incidents at American infrastructure companies over the past two years. Oh, wait – that wasn’t 2021 – it was 2012. The same year that a London business lost over a billion dollars as a result of state-sponsored cyber-attacks.
In 2009 U.S military UAV data was hacked by Iraqi insurgents using laptops and $24.99 file-sharing software, allowing them to see what the UAV had viewed. The year before, DOD and CENTCOM classified networks were hacked. It took days to wrest control back and resecure the nets.
In 2007, Chinese hackers stole project data for the F-35 fighter jet. Two years earlier, it was Space Shuttle Discovery. And in 2003, they stole nuclear weapons test and design data from China Lake.
So – Is This What World War Three Is Going To Look Like?
Maybe. Or maybe it’s what WWIII already looks like.
We’re not a nation of farmers and small, isolated communities – we’re a distributed behemoth with far-reaching interdependencies. Global supply chain issues during the pandemic have made some items difficult to get, and we’ve begun to be aware of just how stretched we are. Recent cyberattacks like the Colonial Pipeline and JBS Meat Distributors have made more people aware of just how easy it would be to disrupt not just travel, but our ability to ship food from one place to another. How easy it would be to disrupt medical care, public safety services, and communications.
The incidents listed in the last section come from a list maintained by the Center for Strategic & International Studies. The web page only shows the last couple of years. The PDF version of the list, however, goes back for two decades. It’s more than 60 pages long, beginning with that China Lake incident in 2003.
Me, I’m in sitting in an uncharacteristic heatwave in Seattle, the least air-conditioned metro area in the country. And I can’t help but think about the fact that China Lake took place in 2003 – the same year that a “software bug” caused a four-day power outage affecting most of the Northeastern United States and some of Canada.
How exactly do you say сладкий как сахар in Chinese?
*about сладкий как сахар
tr: sweet as sugar
say: “sladkiy kak sakhar”
Among military translators, it’s not uncommon to hear this spoken with the accents slightly misplaced, making it resemble an English epithet. That is absolutely how it is used in this post.



I loved how you pulled all this data and information together. Well done, quite realistic, and downright scary for what the “now” and the future look like, and the powers that can be setting this up, and the long-range vision. Thanks for writing and sharing.
and then, today, this appeared in the Guardian…
https://www.theguardian.com/world/2021/jul/15/kremlin-papers-appear-to-show-putins-plot-to-put-trump-in-white-house
Thanks for reading! Long range vision indeed.